The Networx contracts require a basic level of security management for its contractors that ensures compliance with Federal Government generally accepted security principles and practices, or better. The contracts employ adequate and reasonable means to ensure and protect the integrity, confidentiality, and availability of Networx services, Operational Support Systems (OSS), and Government information transported or stored in the contractor's Networx services infrastructure. These requirements are detailed in Section C.3.3.2 Security Management of the Networx contracts.
In addition to this mandatory level of security, the Networx contracts provide additional security services that may be ordered on a fee-for-service basis.
These are:
The MFS offering is described below.
MFS builds on the FTS2001 contracts offerings. The service is implemented to secure internal Agency networks. MFS allows Agencies to mitigate the increasing network security risks they face. The service is one of the security tools that will help reduce service disruptions caused by malicious access, and prevent unauthorized access to or from private networks, such as Local Area Networks (LANs).
MFS safeguards internal networks and systems from hostile activity, protecting critical data from compromise and tampering. As buffers between trusted internal networking environments and external networks, firewalls inspect traffic according to a set of defined security policies, blocking all traffic not meeting the Agency's criteria.
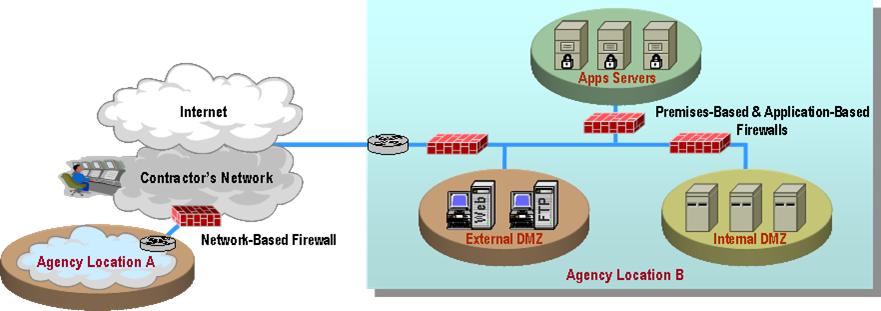
MFS connects to and interoperates with the Agency networking environment, including Demilitarized Zones (DMZs) and secure LANs as required by the Agency. The service also supports connectivity to extranets and public networks such as the Internet.
The contractor provides the firewall software and hardware components, as required. The Agency may order one or more of the following:
Premises-based firewalls deployed at the Agency location. Network-based firewalls located in the contractor's infrastructure. Application/proxy-based firewalls positioned and implemented as per agency needs, and monitor traffic at the application layer.
The diagram below illustrates a sample firewall implementation. Illustrative hardware such as edge routers and Agency servers are not provided as part of the MFS.
MFS also offers several features that complement the basic service. They are
These features are described in Section C.2.10.1.2 Features of the Networx contracts.
MFS provides Agency's internal networks with a layer of protection against cyber attacks. This includes providing Agencies with real-time monitoring that helps mitigate attacks and maintain the availability of Agency mission-critical resources; and a single point of accountability for designing, implementing, managing, monitoring, and maintaining the security solution.
MFS will support the full range of technical capabilities that are available in commercial offerings. These include implementing firewall security policies according to the Agency's needs, proactively monitoring the firewall components on a 24x7 basis, and detecting suspicious activity and policy violations. MFS employs various protection techniques, including but not limited to Stateful Packet Inspection, Network Address Translation (NAT) and Port Address Translation (PAT), to guard the Agency's networks from attacks. The service also uses best practices against Denial of Service (DOS), Ping of Death, IP Spoofing, SYN Flood, and Tear Drop attacks. These and other service capabilities are detailed in Section C.2.10.1.1.4 Technical Capabilities of the Networx contracts.
MFS is required to support the User-to-Network Interfaces (UNIs) defined in applicable Networx services, for example:
Each Networx contractor may provide variations or alternatives to the offering and pricing for MFS. The specific details can be found within each Contractor's Networx contract files and pricing notes for MFS.
For more information on the general MFS specifications and requirements, please refer to Section C.2.10.1 of the Networx contract for technical specifications and Section B.2.10.1 for pricing.
MFS builds on the FTS2001 contracts offerings. MFS provides the following components:
Premise-based and network-based MFS basic services are available in the following three Tiers:
Price components required for service are:
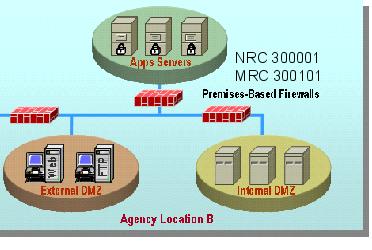
Example 1: Premise-based MFS providing firewall support up to 10 Mbps and up to 100 IP addresses:
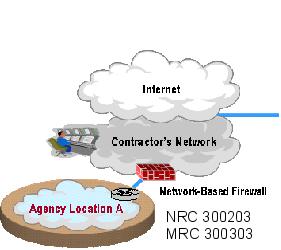
Example 2: Network-based MFS providing firewall support up to 500 Mbps and up to 2,000 IP addresses:
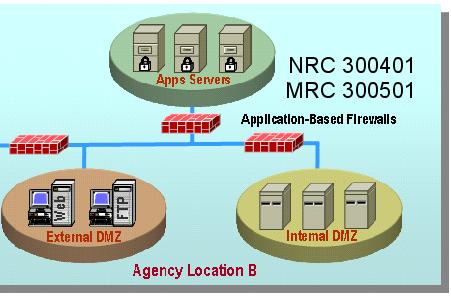
Example 3: Application/proxy-based firewall:
Each Networx contractor may provide variations or alternatives to the offering and pricing for MFS. The specific details can be found within each Contractor's Networx contract files and pricing notes for MFS.
For more information on the general MFS specifications and requirements, please refer to Section C.2.10.1 of the Networx contract for technical specifications and Section B.2.10.1 for pricing.